Doing the basics goes a long way in keeping your personal accounts secure. This first1 edition, started July 2021, of the Personal Infosec & Security Checklist provides actionable security best practices anyone can use to harden their security posture. This list is far from exhaustive, incomplete by nature since the security you need depends on your risks and threats.
⚙️ Improve account settings beyond defaults
For your high value accounts, turn on the highest vendor provided security settings.
For example, if you use Google, turn on “Advanced Protection” which mandates the use of hardware MFA keys only among a slew of other security sensitive settings.
Read more:
Use MFA/2FA everywhere possible.
Prefer to use a hardware device over an authenticator app. Hardware devices are now supported across a wide variety of services such as Dropbox, GitLab, Epic Games, Coinbase, domain registrars, cloud providers and so on. Only use a reputable authenticator app such as Google Authenticator or Authy. If possible, do not use SMS as an account recovery or for MFA/2FA (see SIM takeover precautions below.) Be sure to enable MFA/2FA everywhere — not just some limited set of accounts or services, this helps prevent lateral account takeovers that might not be immediately obvious. Use multiple devices or methods as a backup in case the primary device is lost or destroyed. Safely keep generated backup codes.Read more:
https://www.yubico.com/works-with-yubikey/catalog/
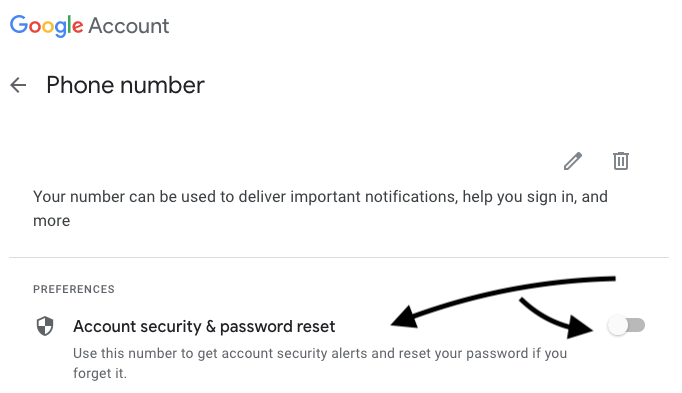
Turn off SMS/phone call account recovery and 2FA/MFA if possible.
Many services require a phone # when signing up which then gets used as an account recovery mechanism. Given how prevalent SIM takeover attacks continue to persist, many services now offer the ability to disable using phone/SMS as an account recovery channel. Be sure to keep recovery codes and linked accounts used for recovery secure as well.
Read more:
Improve your password hygiene.
- Use a password manager.
- Never reuse passwords.
- See above — use a password manager.
- Prefer password length over complexity. When using long passwords (e.g. 32+ characters), double check the password continues to work. Sites will silently truncate input fields, have different restrictions on the password change input fields vs the login fields, etc. After rotating passwords, logout and log back in to ensure the password you intended to set is actually set.
- Assume all of your old passwords are out there in plain text. They are linked to your email and collated across numerous services. Also assume in many cases, for the same service, if you’ve rotated passwords all of the previous passwords are also out there in plain text.
Treat account security recovery questions such as “What’s your favorite ice-cream?” as passwords.
Generate and save responses in your password manager.
Periodically review and purge unused “connected apps”.
Review permissions external apps have to your email, calendar, contacts, etc. Similarly, review permissions and apps you have connected to side-projects, code repos, CI systems, domains, etc.
Read more:
https://myaccount.google.com/permissions [Google] Apps with access to your account https://github.com/settings/applications [GitHub] Authorized applications
Periodically review and purge unused email filters.
Remove old (or surreptitious) filters and rules that might be automatically hiding or forwarding emails to other accounts.
Read more:
Prefer to not login to any of your accounts using someone else’s computer, phone, or device.
Change your password from a trusted computer afterward if you login using an untrusted device. Be sure to logout and invalidate all logged in sessions.
If you use a custom domain for your email, ensure the registrar account is secured with MFA.
Ensure the billing has a backup credit card to prevent interrupting payment remittance. If the DNS/NS settings point to another provider, ensure that that provider is also secured with MFA. Ensure that billing is uninterrupted there as well. Ensure that privacy settings are enabled on the domain so as to not reveal any information that could be used to socially engineer a transfer. Ensure that domain transfer locks are turned on. Ensure that MX records are not duplicating mail elsewhere.
Be careful with email auto-replies or vacation auto-responders.
Don’t inadvertently leak sensitive information to anyone that emails you.
🌐 Web Browsing
Familiarize yourself with modern phishing, scams, and other social engineering attacks.
Stay vigilant and skeptical of all emails, phone calls, letters, and other ways to part you from your data and credentials.
Read more:
https://blog.coinbase.com/phishing-attacks-and-how-to-not-fall-victim-42b489d77199
https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
Make sure you’re on the site you’re intending to be on.
Don’t get tricked into sending credentials to the wrong site. Use bookmarks to save known-good URLs and only use those when visiting the sites. Don't click through suspicious text messages, emails, or other alerts.Don’t run commands in the terminal or browser console that you don’t fully understand.
Commands that someone else is telling you to run at the terminal or console can substantially erode your account and device security.
Remove unnecessary or unused browser extensions and addons.
There is a long and active history of extensions being sold to new owners whose updates might include things you did not initially sign up for.
Don’t install software from non-trusted sources.
Read more:
Beware of revealing passwords when screen sharing, on a video call, or screen recording.
Don’t inadvertantly reveal your password a character at a time. Modern mobile OSs will turn off the trailing show-character when typing a password if screen recording is turned on, but stay vigilant. If you need to log in to an account while sharing your screen, turn the video feed off if you think a secret or credential might be shown. Be equally alert if an MFA QR code is on the screen, API keys, personal-access-tokens, or any other bearer tokens.

📱 Mobile Device
Set up a mobile carrier PIN and port lock out.
Prevent your phone number from being transferred out of your control.
Read more:
https://about.att.com/pages/cyberaware/ni/blog/porting
https://krebsonsecurity.com/2018/02/how-to-fight-mobile-number-port-out-scams/
https://www.thebalanceeveryday.com/prevent-your-mobile-number-from-being-ported-4160360
Use a longer passcode on your phone.
Minimum of 10 digits, prefer over 12 digits. The longer the better.
Read more:
https://www.vice.com/en/article/59jq8a/how-to-make-a-secure-iphone-passcode-6-digits
Encrypt your device.
Read more:
https://spreadprivacy.com/how-to-encrypt-devices
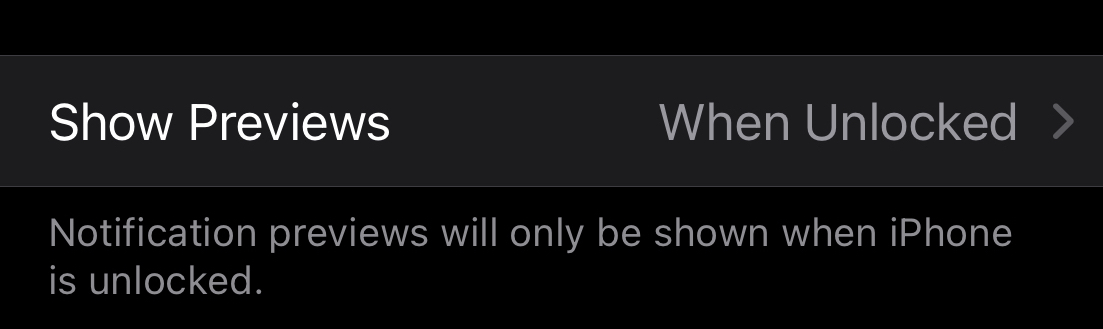
Don't show notification payload on lock screen.
Restrict what someone can see/do with your phone from the lock screen. Don’t show the content of the message on the lock screen if phone is locked. Restrict access to lock screen widgets, notification privacy, Apple Pay/Android Pay/Samsung Pay.
Read more:
iPhone: https://www.ikream.com/hide-messages-on-iphone-lock-screen-28039
Android: https://www.digitalcitizen.life/how-hide-contents-sensitive-notifications-android/
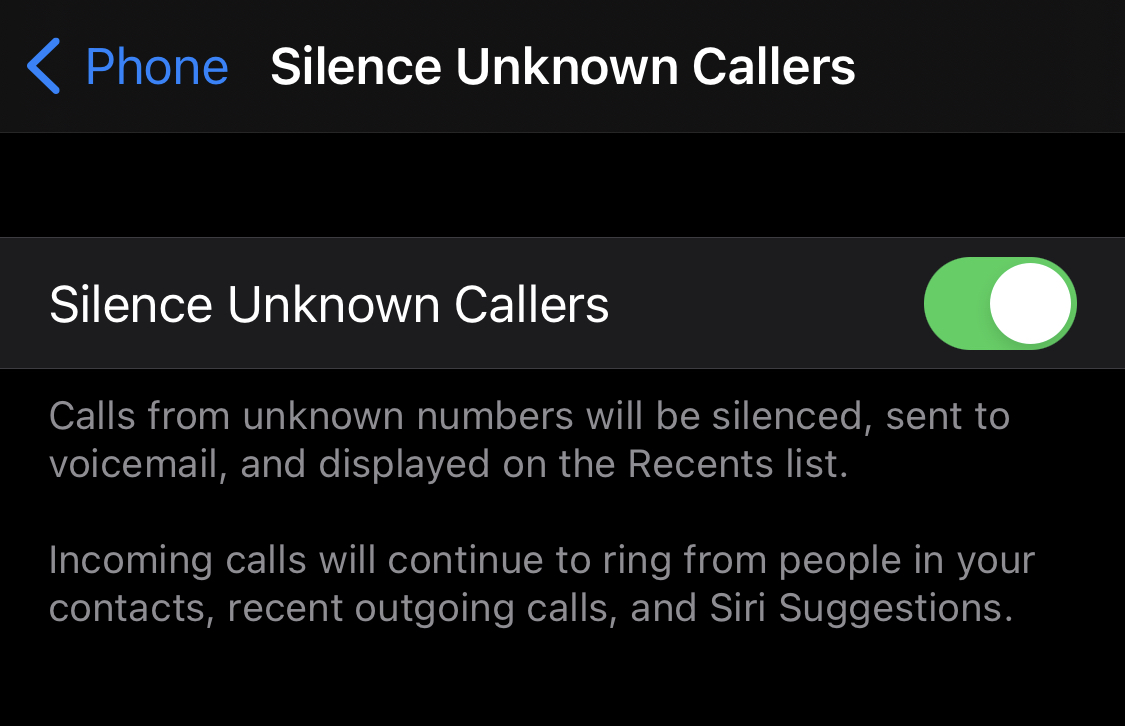
Silence all unknown callers.
Send all phone calls that aren’t in your contacts straight to voicemail. Don’t fall for scam calls. Let them leave a voicemail. Validate the call back number is actually associated with the entity that’s stated.
Read more:
Consider using throwaway phone numbers.
You can easily use throwaway numbers for some use cases such as reward points and other low priority sources. (999) 999-9999, 555-1212, 867-5309, (281) 330-8004
Read more:
https://www.reddit.com/r/LifeProTips/comments/1hkq4i/lpt_dont_have_a_particular_stores_reward_card/
Be careful of phone charging threats.
Prefer to use your own charger and cable.
Read more:
https://www.fcc.gov/juice-jacking-dangers-public-usb-charging-stations
Enable remote device wipe.
Enable Find My iPhone or Android Device Manager to use remote wipe if your phone is stolen or lost.
Read more:
https://support.google.com/accounts/answer/6160491?hl=en
https://support.apple.com/guide/icloud/erase-a-device-mmfc0ef36f/icloud
Enable “Erase Data” to delete data after 10 failed passcode attempts.
Read more:
https://support.apple.com/guide/iphone/set-a-passcode-iph14a867ae/ios
Be aware of and educate yourself about stalkerware.
Read more:
Delete old unused apps.
Be sure to backup any app-specific data you might want to keep.
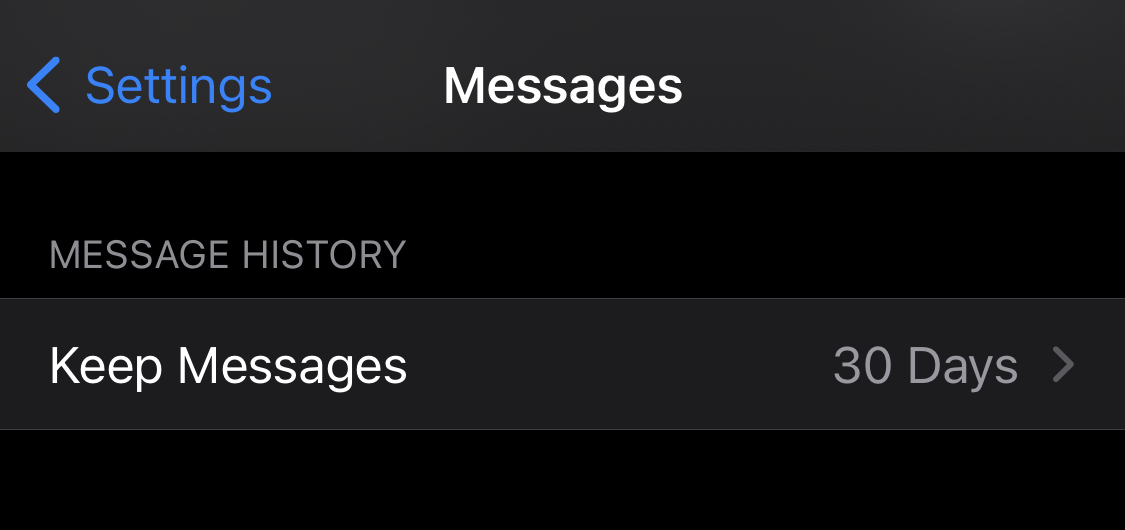
Automatically delete old messages.
Don’t keep sensitive data you no longer need laying around. Delete old text messages, chats, and emails.
Periodically review SMS/text message forwarding settings.
Ensure they are up to date and what you expect them to be.
Read more:
💻 Computer
Encrypt your devices and disks (& power-off instead of hibernate)
Read more:
FileVault Mac
BitLocker Windows - Related: Power off computer, instead of standby
LUKS Linux
Keep your system up to date and apply security patches when they become available.
Read more:
https://docs.microsoft.com/en-us/troubleshoot/windows-client/deployment/keep-windows-up-to-date
https://support.apple.com/guide/mac-help/get-macos-updates-mchlpx1065/mac
Be careful plugging unknown external devices into your computer.
Read more:
Activate screen-lock when idle.
Require a password when resuming from screensaver.
Read more:
https://it.cornell.edu/device-security/set-your-windows-computers-screen-lock-automatically
Learn the keyboard shortcut to lock your computer.
-
Windows logo + L - Windows
-
ctrl + alt + L - Linux
Review your installed apps and remove old ones.
Old and unpatched software no longer being used ought to be uninstalled.
Don't use root/admin account for day to day or non-admin work.
Avoid using the root or admin account for normal day to day work.
Disable Undesired Features (Windows) e.g. MS Office Macros.
Read more:
Enable and use Secure Boot (Windows).
Read more:
Keep multiple backups of your important data.
Read more:
Delete old sensitive data that you don’t need any more—including from old backups.
Don’t keep sensitive data you no longer need laying around. Delete old files, archives, and storage devices.
⚔️ Physical security
Never leave a device unattended, in the trunk, or hidden in a car.
Just bring it with you, no matter how short of a time you’re leaving it there.
Read more:
https://observer.com/2019/11/bluetooth-scanner-car-burglary-stealing-laptops/
Consolidate external hard drives and USB drives so you have fewer things to keep track of.
Wipe and destroy unused old computers, phones, tablets, hard drives, etc.
Consolidate notebooks and papers that could have sensitive info.
Shred and destroy the ones you don't need.Keep back up Titan/Yubikeys in a safe deposit box or offsite.
Backup MFA/2FA devices ought to be kept offsite.
💡 Miscellaneous
Delete/archive old projects, domains, DNS records.
Dangling records and projects can be used in a variety of ways to compromise your security or rack up charges. Use your credit card statements to review for recurring charges you might have forgot about to surface dormant projects/domains that are still running.
Audit your MFA/2FA usage to ensure it’s enabled and up to date.
- Google/Apple ID
- GitHub/GitLab
- Banking
- Coinbase/crypto wallets
- Amazon (retail)
- Amazon/GCP/Azure/Cloudflare (cloud)
- Domain registrars/DNS/web hosting providers
- Whatsapp/Signal/Telegram
- Dropbox
- Slack - all of your Slack teams!
- Twitter/Facebook/Instagram
Thoughts on using VPN not improving personal security or privacy.
Read more:
📚 Further reading
Read stories of others’ account takeover, hacks, and the lessons they learned.
- Getting Hacked, Lessons Learned - AVC, Fred Wilson
- How to lose $8k worth of bitcoin in 15 minutes with Verizon and Coinbase.com - Cody Brown
- How I got hacked, lost crypto and what it says about Apple’s security. Part 1 - Raman Shalupau
👉 Others in the checklist series
1 CCA ShareAlike 4.0 International. This guide is open source via CCA. Your contributions and additions are appreciated!




